Investigating HVNC Attacks

HVNC Attacks allow attackers to work comfortably on their victims’ machines. Let’s investigate such attacks.
Read more
HVNC Attacks allow attackers to work comfortably on their victims’ machines. Let’s investigate such attacks.
Read more
Pink Thumb 2023
– displays a pink thumb on pages you consider save
– warns on untrusted websites that contain a password field
– has a secret defender for endpoint feature
Read more
Let’s go quickly through an example in which an attacker has code execution on a Windows 10 box and opens a proxy channel to an attacker machine. The attacker then uses ‘proxychains’ which ingests all network output from defined tools on the attacker machine into the proxy tunnel to the Windows 10 box.
With that, we will be able to start an RDP session on the attacker machine, proxy it through the Win10 machine to the local Domain Controller.
The result of that is a Domain Controller that only sees an RDP connection coming from the Win10 box and no MSTSC process on this Win10 box. Please, read the last sentence again. This makes the detection of the attacker steps harder
Read more
If you are interested in windows protection and detection techniques and how they behave under the various attacks on Windows credentials, this article is for you.
Read more
People that start working with Defender for Endpoint (MDE) often ask the question “where should I start when I see an alert in MDE?”. There is lot of valuable information available in the portal to help judge if an alert is a real incident or a false positive. Additionally, you can query the raw telemetry via KQL. But there is still lot of room for interpretation. So, what should you do to get started? And what is even more important: how do I keep the overview?
Read more
Version 2 of Gundog to hunt in Microsoft 365 Defender via PowerShell is now available. This article describes the new features.
Read more
In my experience, people – due to a lack of knowledge or plain laziness (and I am one of them) sometimes mix-up terms like Events, Alerts, Alarms and Incidents in their conversations. In addition, different tools have different terms for the objects they are displaying in their GUIs. With this article, we will go through all those entities in Sentinel and take a deep dive into their correlations.
Read more
With Microsoft 365 Defender, we not only know that a phishing link was received but also that the user clicked on it – however, what we do not know is: if the user provided his credentials to the shady site he clicked on. How do we handle such alerts?
Read more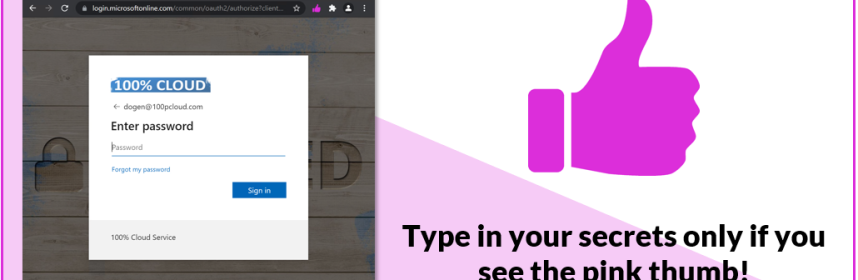
To help users to make better decisions, when to type a password / on which sites, I have created a very simple chrome extension (that also works on edge): PINKTHUMB – only type in your password when its pink!
Read more
The Azure Sentinel community is great. Many people contribute to the Azure Sentinel GitHub site. Rod Trent wrote an article on how to deploy analytic rules from GitHub to your Sentinel instance. This is great, however, the rules are written in YAML and can therefore easily be imported programmatically.
Read more